mirror of
https://codeberg.org/forgejo/forgejo.git
synced 2025-03-24 04:21:34 -05:00
Include the GITHUB_TOKEN/GITEA_TOKEN secret for fork pull requests (#26759)
Include `GITHUB_TOKEN`/`GITEA_TOKEN` secrets for actions triggered by
pull requests
This makes it consistent with the environment variables which you can
already access
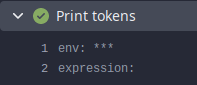
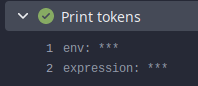
```shell
echo env: $GITHUB_TOKEN
echo expression: ${{ secrets.GITHUB_TOKEN }}
```
before
after
---------
Co-authored-by: Jason Song <i@wolfogre.com>
Co-authored-by: Giteabot <teabot@gitea.io>
This commit is contained in:
parent
b91057b172
commit
4f5a2117c3
1 changed files with 5 additions and 8 deletions
|
|
@ -55,8 +55,12 @@ func pickTask(ctx context.Context, runner *actions_model.ActionRunner) (*runnerv
|
|||
|
||||
func getSecretsOfTask(ctx context.Context, task *actions_model.ActionTask) map[string]string {
|
||||
secrets := map[string]string{}
|
||||
|
||||
secrets["GITHUB_TOKEN"] = task.Token
|
||||
secrets["GITEA_TOKEN"] = task.Token
|
||||
|
||||
if task.Job.Run.IsForkPullRequest && task.Job.Run.TriggerEvent != actions_module.GithubEventPullRequestTarget {
|
||||
// ignore secrets for fork pull request
|
||||
// ignore secrets for fork pull request, except GITHUB_TOKEN and GITEA_TOKEN which are automatically generated.
|
||||
// for the tasks triggered by pull_request_target event, they could access the secrets because they will run in the context of the base branch
|
||||
// see the documentation: https://docs.github.com/en/actions/using-workflows/events-that-trigger-workflows#pull_request_target
|
||||
return secrets
|
||||
|
|
@ -82,13 +86,6 @@ func getSecretsOfTask(ctx context.Context, task *actions_model.ActionTask) map[s
|
|||
}
|
||||
}
|
||||
|
||||
if _, ok := secrets["GITHUB_TOKEN"]; !ok {
|
||||
secrets["GITHUB_TOKEN"] = task.Token
|
||||
}
|
||||
if _, ok := secrets["GITEA_TOKEN"]; !ok {
|
||||
secrets["GITEA_TOKEN"] = task.Token
|
||||
}
|
||||
|
||||
return secrets
|
||||
}
|
||||
|
||||
|
|
|
|||
Loading…
Add table
Reference in a new issue

